Iranhumanrights.org – Suspected state-sponsored hackers have intensified their attempts to break into the online accounts of Iranian rights activists in recent weeks by exploiting security vulnerabilities in Android smartphones, the International Campaign for Human Rights in Iran has learned.
On August 11, 2016 an unknown person sent a message on Facebook to a prominent Iranian political activist living in Paris and introduced himself as a former student. The hacker said he had created political stickers with the activist’s photo on them. He then sent a file, with an APK suffix, to the activist claiming that the file contained the stickers.
Soon after the activist opened what was really a malware file, the hacker took over the victim’s Facebook page and sent similar messages to the activist’s friends, some of whom worked at Radio Farda, Deutsche Welle and the BBC. One of the victim’s friends fell for the trap and lost access to his Gmail account for several hours.
Files with the APK suffix are applications that can be installed on smartphones with Android operating systems. Users should only open these files after downloading them from reputable sources, such as Google Play. Unlike Apple’s iOS operating system, Android apps can be independently developed and installed, presenting an opportunity for hackers to prey on unsuspecting users and spy on them.
The file that was used to hack into the Paris-based activist’s account was created by DroidJack, an Android “Remote Administration Tool” that allows hackers to build trojan programs designed to breach the security of a computer system while ostensibly performing another function.
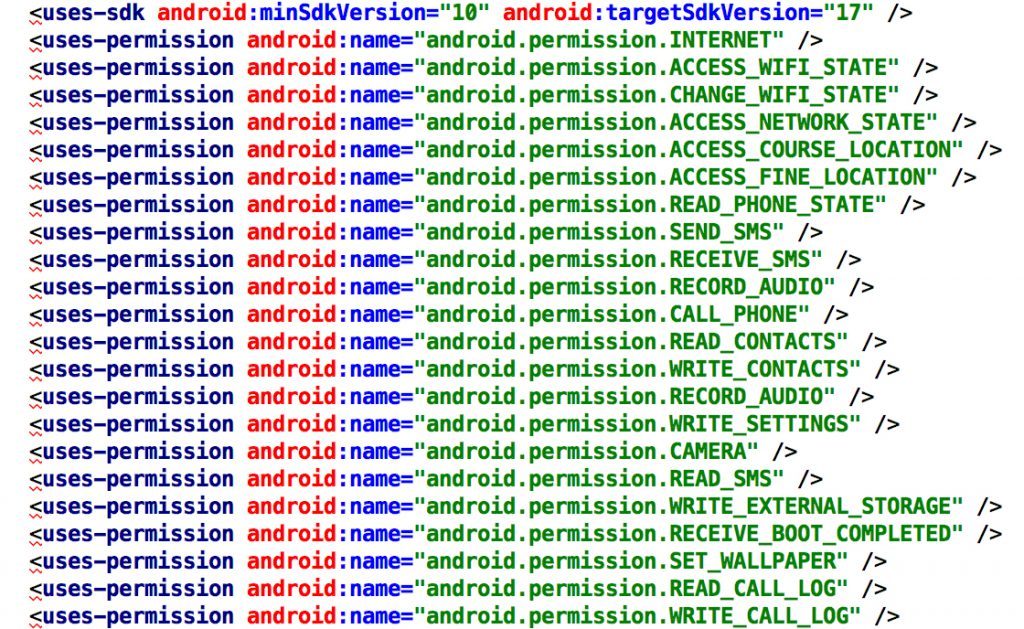
List of locations accessed by hackers on a victim’s Android smartphone.
Investigations by the Campaign show that trojan malware created by hackers gain remote access to a wide range of content on Android smartphones including messages, photos, audio files, apps, GPS locators, and contact lists. The hackers can monitor conversations and operations on the device without the owner’s knowledge and make phone calls and send messages.
The hacking victim’s photo was placed in the malware file to trick him into downloading it.
Previously the Campaign had revealed that hackers were tricking victims into downloading false IMOchat program installers to gain access to their accounts. These malware files were created byMetasploit, an Android penetration testing software. Hackers have also sent messages on Facebook to Iranian journalists living abroad and asked them to click on false links on Google Drive to “receive important urgent news.”
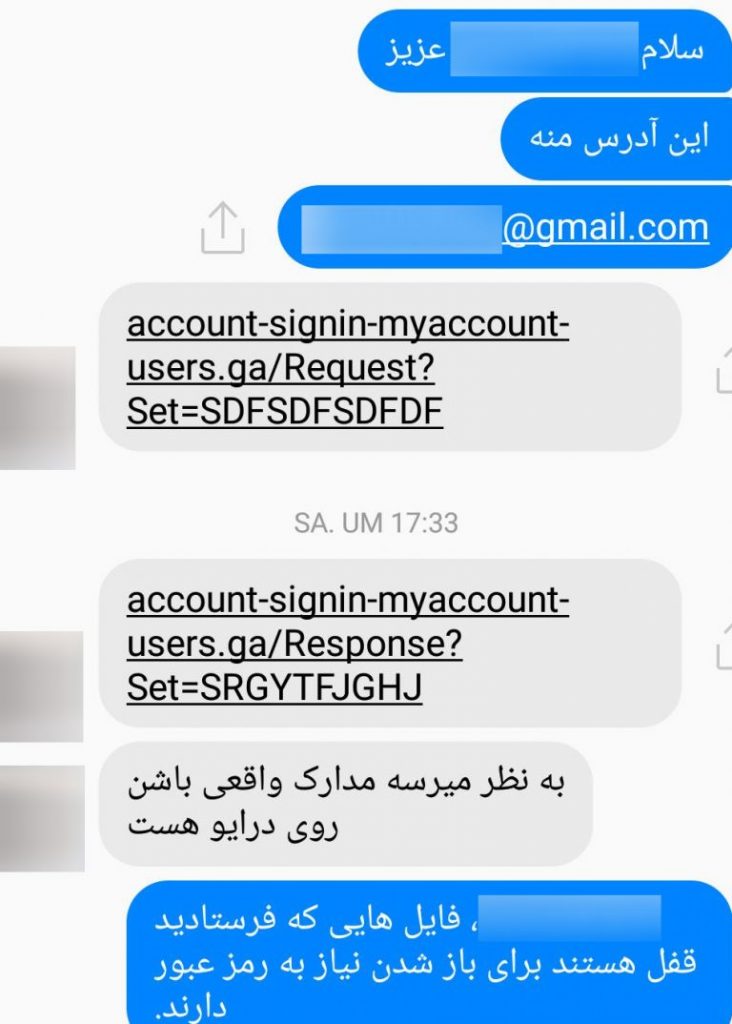
Message sent to journalists from a hacked account.
The journalist whose Gmail account was hacked described the following process to the Campaign:
1- Hacker directs unsuspecting victim to false Google account sign-in page.
2- Victim enters username and password.
3- Hacker records victim’s username and password and submits an access request to Google.
4- Google sends a text message to the victim to complete the two-step verification process.
5- Victim inputs the verification code in the false Google sign-in page.
6- Hacker copies the verification code, which is valid for only 30 seconds, and signs into the victim’s account.
 Shabtabnews In this dark night, I have lost my way – Arise from a corner, oh you the star of guidance.
Shabtabnews In this dark night, I have lost my way – Arise from a corner, oh you the star of guidance.